Scan Linux Backups for Malware
- Brad Linch

- Apr 10, 2021
- 2 min read
Updated: Aug 23, 2021
I can still feel the buzz in the air from Veeam's v11 release. We are approaching two months since the GA annoucement, and the excitement around CDP (Continuous Data Protection), Linux Hardened Repository and object storage enhancements hasn't let up. With that said, I want to highlight a v10 feature that never received the love it deserved - Data Integration API.
What is the Data Integration API?
You can find plenty of content on how the Data Integration API can be used with Windows, but I want to highlight how it can be used with Linux too. For those new to the concept, Data Integration API allows users to easily reuse their backup data. You can mount any virtual (VMware and Hyper-V) or physical (Windows and Linux) backup to a target server of your choosing for malware scans, data mining, devops and many other purposes.

How Can I use it for a Linux Backup?
Once you have a virtual or physical Linux machine backup you simply need to run the below commands in PowerShell. The variables in the script contain the following:
The backup job that contains my Linux machine. Note: you could choose a specific machine rather than a whole job
$backup = Get-VBRBackup -Name "Orcl"The Linux server my backup will be mounted to:
$targetServerName = "198.18.128.102"Credentials to that mount server. I have multiple root credentials so the "where" parameter chooses the one with the description I want. Note: you do not need to be root. I am just a bit lazy with security best practices in my home lab
$targetAdminCredentials = Get-VBRCredentials -name "root" | where {$_.description -eq "root"}The restore point I want to use. In the below example, I am using the most recent restore point
$restorepoint = Get-VBRRestorePoint -Backup $backup | Sort-Object –Property CreationTime | Select -Last 1Publish the backup content
$session = Publish-VBRBackupContent -RestorePoint $restorepoint -TargetServerName $targetServerName -TargetServerCredentials $targetAdminCredentials -EnableFUSEProtocol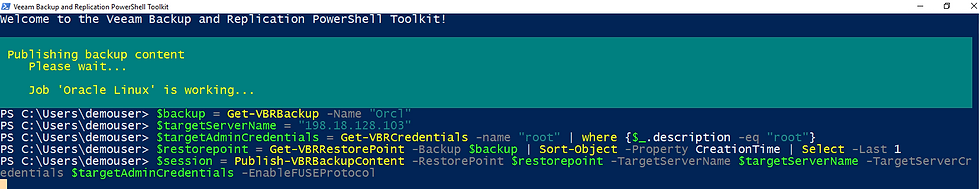
Once the Linux backup contents are published, you can SSH into the Linux mount server and see the file system in /tmp. A great use-case from this point would be to-do an anti-virus scan to ensure your backups are safe from malware.

Personally, I used ClamAV because it was easy to install and free. Plus, you can run an AV scan on a specific directory with ClamAV. I didn't see that option with other free tools. Below is the command I ran on the centos-root directory confirming that the mounted Linux machine is clean of malware.
clamscan -r -i /centos-root
In Veeam a restore session will kickoff, and it should look like the below.

In summary, Veeam's Data Integration API is a great way to check for malware on Linux backups. Veeam's Secure Restore in combination with SureBackup automates this process, but it only works for Windows machines today. Leveraging Data Integration API for Linux backups in conjunction with Secure Restore/SureBackup for Windows is a great method to ensure all backups are useable.




Comments